Asymmetric vs Symmetric Encryption – Key Differences
Have you ever heard of symmetric and asymmetric encryption? Do you know what the difference is between the two? In this post, we will explain symmetric vs asymmetric encryption in easy-to-understand terms, so that you can make an informed decision about which type of encryption is best for your needs. So read on to learn more!
What is encryption and cryptography?
Encryption
Encryption is a process of transforming readable sensitive data into an unreadable format. This is done using an encryption key, which is a string of characters that can be used to encode and decode the data. The encryption key is typically generated using a mathematical algorithm, and it can be either public or private. You can see and generate example keys using online key generators such as devglan.
Encryption is used in order to protect information from being accessed by unauthorized individuals. It is also used to authenticate users and to ensure the confidentiality of communications. The two main types of encryptions in use today are asymmetric and symmetric encryption.
Cryptography
Cryptography is science of making codes and ciphers. It is used to protect information from being read by people who are not supposed to have access to it. Cryptography is used in a variety of different ways, including:
- encrypting messages so that only the intended recipient can read them
- hiding information in images or other files
- creating digital signatures that can be used to verify the author of a document or email
Cryptography is a complex field and there are many different methods that can be used for encryption. All cryptography systems share one essential goal: to ensure that only authorized users can access the information that has been encrypted.
What is symmetric encryption
Symmetric encryption is a way of making sure that the people who are supposed to see your data can see it, and the people who aren’t supposed to can’t see it. This is done by using a key to change the data into an unreadable format. The key is either public or private, and it’s used to encode and decode the data.
How does symmetric encryption work?
The sender uses the key to encrypt the data, and then sends it to the recipient. The recipient uses the same secret key to decrypt the data. The symmetric encryption process is shown in the diagram below.

Secret key (AES 128-bit) example: s6v9y$B&E)H+MbQeAs you can see, symmetric key encryption is a simple and efficient way to encrypt data. However, there are a few drawbacks to this method. First, both the sender and the recipient must have the same key. This can be difficult to manage, especially if there are a large number of users. Second, if the key is lost or stolen, the data can be easily decrypted by anyone who has it.
Symmetric encryption algorithms
Symmetric encryption algorithms are the algorithms that are used to perform symmetric key cryptography. There are a variety of different symmetric encryption algorithms, including the following:
AES
The Advanced Encryption Standard (AES) is a symmetric encryption algorithm that was developed by the National Institute of Standards and Technology (NIST). It is a 128-bit algorithm, which means that it can encrypt data up to 128 bits in length. AES is considered to be one of the most secure encryption algorithms in use today.
DES
The Data Encryption Standard (DES) is a symmetric encryption algorithm that was developed by IBM in the 1970s. It is a 64-bit algorithm, which means that it can encrypt data up to 64 bits in length. DES is no longer considered to be a secure encryption algorithm, and it should not be used for any new applications.
3DES
Triple DES (3DES) is a symmetric encryption algorithm that was developed as an improved version of DES. It is a 128-bit algorithm. 3DES is considered to be a secure encryption algorithm, but it is slower than AES.
RC4
The Rivest Cipher 4 (RC4) is a symmetric encryption algorithm that was developed by Ron Rivest in 1987. It is a stream cipher, which means that it encrypts data one byte at a time. RC4 is considered to be an insecure encryption algorithm, and it should not be used for any new applications.
What is asymmetric encryption
Asymmetric encryption also known us public key encryption is a more secure way of encrypting data. It uses two different keys – a public key and a private key – to encode and decode the data. The public key can be shared with anyone, while the private key should be kept secret.
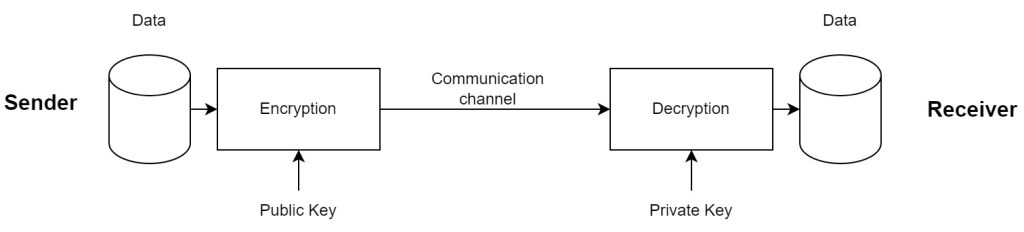
How does asymmetric encryption work?
The sender uses the public key to encrypt the data, and then sends it to the recipient. The recipient uses the private key to decrypt the data. This process is shown in the diagram below.
RSA 1024-bit example
Private key:
MIICWwIBAAKBgGeZDIQEe12WWGKWAwmiQVi95bsckbTQ4ffn6pOLCLEa7bW3/v296AGaj27EmocPbXQF22mFjz44zrm0fHaTOR4vP2tSRV6lu5ih7GTdsKVgTzKtu877dVgib4MEmJzKGRxjyArIw8c11nbV+NHfhsBVPxXgjvPHGw6N/YnjCRezAgMBAAECgYAbXBQuGXDrOnWFM9EBjlRrt1sgm17vveqvqhQNez6EZ3Q39avmH21SXxtaSZn16WEirxlPOPKnoCEYck4ckq0WsYZ9ZDESdj5oryc3fALvq/XUSuniYq92vaQnooGZaByf8ioVhAyXNQC6luWj3iwMbm4iL0rNr4o98agOfFn3QQJBAKvv1KciuqovUhTIr3VjbGblX+6UxcrAQ68AnPx23pYvD7ErWqj0zSV9FMrH81jHf+wBqo427Z90m0WmZ6lEeQsCQQCaP7CK2tYLglocfm0fBYVuAJFcMve6h9ujQOjkM41tRc+os6Xqpgv3gGCwQNyTpVvThMLcxYVhdDLa6uv3f5T5AkA0NIbyFJZu9B1NGD5GO2D/wSemrl98F3K1oU8JTSJ6oWF3Xv2RDXt4pYj5pUqbK0AJLdxWgBEYeHRo6oTRHWxPAkBuouYfAo3qnWnC7E+ao5wr5Y5dolUb3tyEQUeKfwue6Cbla03De6wzr0oqwas037N4iM44Chj8aJsdeMkdsc4JAkEAnHDL4SNw8A5hYcca8SZN6jNBxX8sQwvfs4cqk1PXCmqh+VAfktAoPjLtRkK9C9wx7qDljHXvIVnH5O60VdGroQ==
Public key:
MIGeMA0GCSqGSIb3DQEBAQUAA4GMADCBiAKBgGeZDIQEe12WWGKWAwmiQVi95bsc
kbTQ4ffn6pOLCLEa7bW3/v296AGaj27EmocPbXQF22mFjz44zrm0fHaTOR4vP2tS
RV6lu5ih7GTdsKVgTzKtu877dVgib4MEmJzKGRxjyArIw8c11nbV+NHfhsBVPxXg
jvPHGw6N/YnjCRezAgMBAAE=Asymmetric encryption is secure encryption because it uses two keys. This makes it more difficult for someone to decrypt the data without the private key.
Asymmetric encryption algorithms
There are a variety of different asymmetric encryption algorithms that are used in public key cryptography, but some of the most popular are the following:
RSA
The Rivest-Shamir-Adleman (RSA) algorithm is an asymmetric encryption algorithm that was developed by Ron Rivest, Adi Shamir, and Leonard Adleman in 1978. It is the most popular asymmetric encryption algorithm in use today, and it is used to encrypt data of any length. RSA is considered to be a secure algorithm, and it is widely used in both commercial and government applications.
ECC
Elliptic Curve Cryptography (ECC) is an asymmetric encryption algorithm that was developed in the 1990s. It is based on elliptic curve theory, which allows for smaller keys sizes than traditional RSA cryptography. ECC is considered to be a secure algorithm.
Diffie-Hellman
The Diffie-Hellman algorithm is an asymmetric encryption algorithm that was developed by Whitfield Diffie and Martin Hellman in 1976. It is used to generate a shared secret between two parties, which can then be used to encrypt data. Diffie-Hellman is also considered to be a secure algorithm.
DSA
The Digital Signature Algorithm (DSA) is an asymmetric encryption algorithm that was developed by the National Institute of Standards and Technology (NIST) in 1991. They are mainly using it to create digital signatures, which verify the authenticity of a message. DSA is a secure algorithm, and both commercial and government applications are making use of it.
Asymmetric vs symmetric encryption – Key differences
Comparing asymmetric vs symmetric Encryption is like comparing a locked room with one key to a locked room with two keys. Both encryption types use cryptographic keys, and their goal is to protect information, but each has its own advantages and disadvantages. Below we will take a more in-depth look at symmetric vs asymmetric encryption, as well as the advantages and disadvantages of each type of encryption.
| Key Differences | Symmetric Encryption | Asymmetric Encryption |
| Number of keys | The same key is used to encrypt and decrypt data | Two different keys are used to encrypt and decrypt data |
| Speed | Faster than asymmetric encryption | Slower than symmetric encryption |
| Security | Less secure than symmetric encryption | More secure than symmetric encryption |
| Data size | Can be used for both small and large amounts of data | Typically only used for small amounts of data |
| Complexity | Less complex | More complex |
| Use Case | Symmetric encryption is typically used for communication between two parties | It is often used for authentication and digital signatures |
| Vulnerable to key brute force attacks | Yes | No |
| Key size | 128/192/256 bits | 1024/2048/4096 bits |
| Algorithms | AES (Advanced Encryption Standard), DES (Data Encryption Standard), 3DES (Triple Data Encryption Standard) RC4 (Rivest Cipher 4) | RSA (Rivest-Shamir-Adleman) DSA (Digital Signature Algorithm) ECC (elliptic curve cryptography) DH (Diffie-Hellman) |
Conclusion
So, which method of encryption should you use? That depends on your needs. Both symmetric and asymmetric encryption have their own advantages and disadvantages, but asymmetric encryption is generally more secure. If you need to encrypt a large amount of data quickly, symmetric encryption is the best choice. If you need to ensure that only authorized users can access the data, asymmetric encryption is the better choice.