What Is Cryptography and How Does It Work? [Beginner Guide]
Cryptography is the practice of secure communication in the presence of third parties. It is used in a variety of applications, including email, file sharing, and secure communications. Cryptography is based on mathematical algorithms that scramble data into an unreadable format. Only the sender and recipient can unscramble the data with the correct key. Cryptography is one of the most important tools for protecting information online. Let’s take a closer look at cryptography and how it works.
How does cryptography work?
Cryptography is the practice of secure communication in the presence of third parties. It is often used in computer security, military communications, and political affairs. It is used to protect electronic information from unauthorized access and to ensure the privacy of communications.
There are two main types of cryptography: symmetric-key cryptography and public-key cryptography.
symmetric key cryptography

Symmetric cryptography is a type of encryption that uses the same key to both encrypt and decrypt data. This key is known as the secret key, and it must be kept safe in order to maintain the security of the data.
There are a few different types of symmetric encryption algorithms, but they all work in essentially the same way. First, the sender encrypts the data using the secret key. Then, they send the encrypted data to the receiver through the communication channel. The receiver decrypts the data using the same secret key. Because both parties have access to the same key, symmetric-key cryptography is sometimes referred to as secret-key cryptography.
Symmetric-key cryptography is a very important part of computer security. It is used in many applications, including email, file sharing, and web browsing. When used properly, it can be very effective at keeping data safe from prying eyes. However, it is important to remember that symmetric-key cryptography is only as strong as the secrecy of the key. If someone else discovers the secret key, they will be able to read any encrypted data. For this reason, it is important to choose a good secret key and keep it safe.
Public-key cryptography
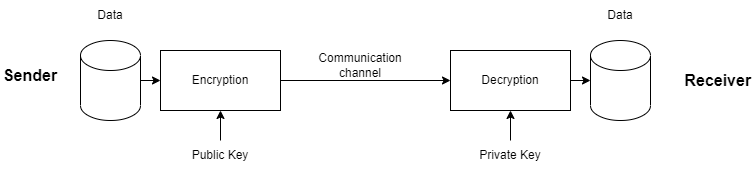
Public-key cryptography, also known as asymmetric cryptography, is a type of cryptography that uses a pair of keys to encrypt and decrypt data. One key, known as the public key, is used to encrypt data. The other key, known as the private key, is used to decrypt data. The public key can be shared with anyone, while the private key must be kept secret. Public-key cryptography is used in a variety of applications, including electronic commerce and email.
Asymmetric key cryptography is based on the principle of security through obscurity. The only way to decrypt data that has been encrypted by the public key encryption is to know the private key. This means that if the private key is not compromised, the data will remain secure.
Public-key cryptography is not perfect. If the private key is compromised, all of the data that has been encrypted with it will be vulnerable. In addition, public-key cryptography is computationally intensive, which can make it impractical for some applications. Nevertheless, public-key cryptography is widely used and considered to be very secure.
The history of cryptography
Cryptography has a long and fascinating history. It is believed to have originated in Ancient Egypt, where hieroglyphs were used to create secret messages. The Greeks also made use of it, and the Roman emperor Julius Caesar is said to have used a simple substitution cipher to communicate with his generals. During the Middle Ages, cryptography was often used by diplomats to encode sensitive information. In the early 20th century, it became increasingly important with the rise of technology. During World War II, it played a vital role in protecting military secrets.
In recent years, cryptography has become increasingly important as more and more information is shared electronically. With the advent of the Internet, it is used in a variety of applications, including email, file sharing, and web browsing. Cryptography is also used to protect sensitive information, such as credit card numbers and medical records.
Principles of cryptography
There are four main principles of cryptography:
- Confidentiality: This principle is also known as the secrecy principle. It states that information should only be accessible to those who are authorized to access it.
- Integrity: This principle states that information should not be modified in an unauthorized or undetected manner.
- Availability: This principle states that information should be available to those who are authorized to access it.
- Non-repudiation: This principle states that individuals should not be able to deny that they performed an action.
Real world examples of cryptography
Cryptography is used in a variety of applications, including email, file sharing, and web browsing.
- Email: it is used to protect email messages from being read by anyone other than the intended recipient. When you send an email, it is encrypted with a public key. The recipient decrypts the message with their private key.
- File sharing: it is used to protect files from being read by anyone other than the intended recipient. When you share a file, it is encrypted with a public key. The recipient decrypts the message with their private key.
- Web browsing: it is used to protect web traffic from being intercepted by anyone other than the intended recipient. When you browse the web, your traffic is encrypted with a public key. The recipient decrypts the message with their private key.
- Cryptocurrencies: Cryptocurrencies like Bitcoin use cryptography to secure transactions.
The differences between cryptography, cryptology, and encryption
Many people assume that cryptography, cryptology, and encryption are three terms for the same thing. However, there are actually some subtle differences between these three fields. Cryptography is the practice of creating codes and ciphers. Cryptologists, on the other hand, work to study and break codes and ciphers. Encryption, meanwhile, is a process of transforming readable data into an unreadable form. This transformation is typically done using a key, which can be used to reverse the process and decrypt the data.
While all three of these fields involve secret communication, they each take a different approach. Cryptography is focused on creating codes, cryptology is focused on studying and breaking them, and encryption is focused on transforming readable data into an unreadable form. As a result, they are each distinct disciplines with their own unique set of tools and techniques
Most well-known cryptographic algorithms
There are a number of different cryptography algorithms, each with its own strengths and weaknesses. Some of the most well-known algorithms include:
RSA
RSA (Rivest–Shamir–Adleman) is a cryptographic algorithm that is used to encrypt and decrypt messages. It is named after its inventors, Ron Rivest, Adi Shamir, and Len Adleman. RSA is a public-key cryptography algorithm that uses two keys: a public key, which is known to everyone, and a private key, which is known only to the recipient of the message. The message is encrypted with the recipient’s public key and can be decrypted with the recipient’s private key. RSA is one of the most popular and widely used cryptographic algorithms. It is used in many applications, including digital signatures, file encryption, and email encryption.
AES
AES (Advanced Encryption Standard) is a cryptographic algorithm that was developed to replace the DES algorithm. AES uses a key that is 16 bytes long, which is longer than the key used by DES. AES also uses a different encryption method than DES, known as Rijndael. AES is faster than DES and is more secure. AES has been adopted by the U.S. government and is used by many businesses and organizations to protect their data.
DES
DES (Data Encryption Standard) is a cryptographic algorithm that was developed in the 1970s. It was originally designed to be used with the U.S. government’s classified information, but it has since been made available for public use. DES uses a 56-bit key, which means that there are 2^56 possible keys that can be used. DES is a symmetric key algorithm, which means that the same key is used for both encryption and decryption. DES is no longer considered to be a secure algorithm, due to its short key length and the fact that it has been broken by higher-powered computers. However, it is still widely used, due to its low cost and ease of implementation.
ECC
ECC is a cryptographic algorithm that is used to generate key pairs. The algorithm is based on the mathematics of elliptic curves with at least 2048-bit keys which are the standard for asymmetric encryption which is used in both public key cryptography and digital signatures. In public key cryptography, ECC is used to generate a shared secret between two parties. This shared secret can then be used to encrypt and decrypt messages. In digital signatures, ECC is used to create a signature that cannot be forged. The algorithm is also used in other applications such as secure communication and authentication.